Thoughts about passwords management
Table of contents
- Intro
- Passwords history
- Data breaches
- How to check my accounts
- Most common passwords
- Consider a password manager
- Critical to know by heart
- World Password Day
- Useful links
Intro
Did you hear something about security breaches, importance of keeping your passwords strong enough and using Multi-Factor Authentication?
Well, of course you did, and I have no doubts you already follow these practices when you sign up on a new website, in a new app or once a service asks you to update your password. In this blog post I will try to explain you everything I learnt about passwords history and give some advices on how to handle them nowadays.
I wrote this simple password generator using Web Crypto API, hence it should be pretty strong and safe enough to use it, despite the fact that it's running straightly in your browser.
You can read more about entropy as a measure of password strength on wikipedia. Overall quality is calculated using zxcvbn utility from Dropbox team. It can be considered as a realistic1 strength estimator.
Passwords history
Passwords have been used in computer systems since their earliest days, and more concrete since 19612 when they were used in CSTT operating system from MIT, that was the first computing system to implement password login. Today, after more than half of a century later, we still use passwords as a go-to way to protect our data and privacy, although there are other ways of doing this. But those are more complex and require user to be more tech-savvy.
The problem is that computers became insanely performant and guessing a password is not that hard anymore, especially if that password is easy to guess. There is a possibility that it was used by someone on a service that experienced a data breach in the past, and if that service wasn't smart enough to hash, salt or encrypt all the passwords of its users, we can end up seeing our password in a so-called Rainbow Tables3.
Data breaches
Last years many companies announce data leaks one after another, no mater how big and secure is the company.
Some noticeable incidents:
- Instagram, TikTok, YouTube in 2020 (235M user profiles)
- Facebook announced 3 data leaks in 2019 (540M or 146GB of members data)
- Uber in 2017 (57M user profiles, 600K driver profiles)
If even such a tech giants cannot protect themselves and their users, what to say about small and medium-sized companies that cannot afford to have a department of security engineers and to spend massive amount of money on security needs.
In some countries fines and punishment for data leaks are so small that it's way more profitable to pay them instead of having a whole security department, paying salaries, taxes and spending money for penetration tests.
For example, in Russia the max fine for leaking users personal data is 100 000 rubbles.
How to check my accounts
The most popular services that aggregate leaked data and allow users to check their Email addresses against potential presence in various data leaks are haveibeenpwned.com and monitor.firefox.com.
If you trust the company behind this service, just enter your Email address to see if it was noticed in former breaches. Mine was for sure.
If you found yourself on one of these services, it's time to check and update your credentials. By the way, they provide a subscription feature and may inform once a new leak will occur.
Do not enter your Email address on websites you don't trust, even if they promote checks against data leaks and guarantee anonymity. Seriously, just don't.
Most common passwords
You may be surprised, but in 2022 people still tend to use unimaginably weak and trivial strings in their passwords, ignoring all the advices they receive and constraints defined by particular services.
Just have a look at these lists:
- NordPass: Top 200 most common passwords of 2021
- National Cyber Security Center: Top 20 most common passwords of 2019
- SplashData: Top 100 passwords of 2017
- 10k-most-common.txt on GitHub
It's funny that most compromised SSH password is root4 of course.
If you don't want to follow those links above, here's a list of top 10 passwords according to NordPass report as of 2021:
| Rank | Password | Time to crack it | Count |
|---|---|---|---|
| 1 | 123456 | < 1 Second | 103,170,552 |
| 2 | 123456789 | < 1 Second | 46,027,530 |
| 3 | 12345 | < 1 Second | 32,955,431 |
| 4 | qwerty | < 1 Second | 22,317,280 |
| 5 | password | < 1 Second | 20,958,297 |
| 6 | 12345678 | < 1 Second | 14,745,771 |
| 7 | 111111 | < 1 Second | 13,354,149 |
| 8 | 123123 | < 1 Second | 10,244,398 |
| 9 | 1234567890 | < 1 Second | 9,646,621 |
| 10 | 1234567 | < 1 Second | 9,396,813 |
Consider a password manager
Good passwords must contain both lower- and uppercase letters, numbers, special characters and have enough entropy (be long). In addition to this, they must be unique and not be reused across many apps. Such a constraints make it close to impossible to keep them all in one head. I would even say managing them in an analogue or digital storage is not an easy task. Imagine having and notebook with 100 credentials (service address, login/email, password, etc.) and updating all of them several times a year.
Thanks to humanity we solved this problem by inventing password managers. Basically, these are tools to help to store, organize keep track, update and protect sets of credentials.
There are 2 sorts of Password Managers: Open Sourced and Proprietary.
Well, it's debatable for sure, but proprietary PMs have exact same downsides as any other app: they store your data, and they are vulnerable to data breaches. Plus they all are paid of course.
Open Source password managers:
Some popular proprietary password managers:
I prefer KeePassXC, just because it is cross-platform, and I can use it on both Mac and Windows machines.
KeePassXC can be installed using brew. Give it a try:
brew install --cask keepassxc
For terminal lovers there are many impressive tools that use GPG encrypted files as a storage. Canonical one is pass. More robust one that looks promising is gopass.
Critical to know by heart
I don't memorize 99% of my passwords, however some of them are very critical to remember, like the one from your password manager or one that you use to log in into your operating system. Basically, those are passwords that should be used without having access to PM.
Usually we think about passwords as random strings of predefined characters. It's true, but not always. There is another technique, called passphrase and such passwords are way easier to remember.
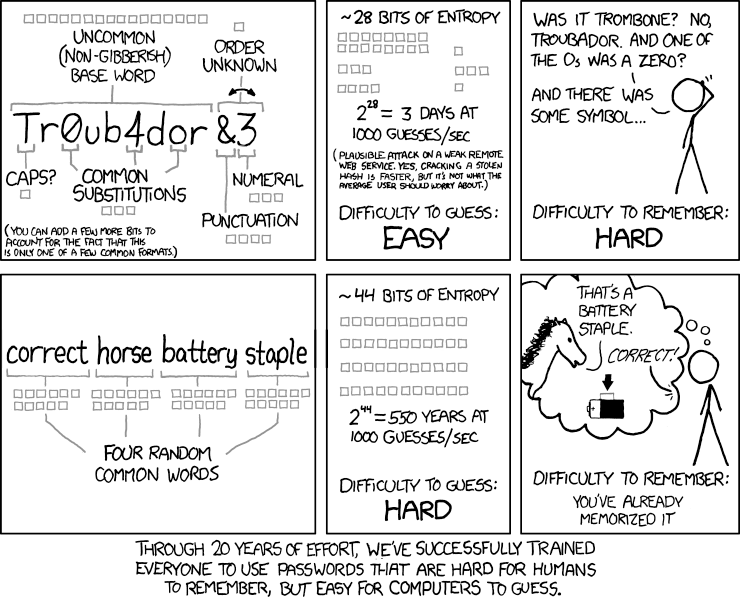
Source: xkcd Password Strength comics
Let's take a look at this passphrase and classic random password I have generated in KeePassXC:
CONSENSUS GONE TRIAL BACKHAND PAYEE and aZa%aj@w5L&X. Even though visually they differ hugely,
and you might think the second one is more secure, it's not.
| Value | Passphrase | Password |
|---|---|---|
| Entropy (KeePass, bit) | 64.62 | 61.44 |
| Easy to remember | ✅ | ⛔️ |
It's obvious that passphrases are easier to remember by creating mnemonics similar to one shown in the comics above. How safe they are? Well, let's calculate the possible number of combinations.
Having a wordlist provided5 by EFF, and using a diceware method for passphrase generation, we have the following numbers:
const wordsCount = 7776; // words count in the EFF list
const passphraseLength = 6; // assuming we generate a 6-words passphrase
const combinationsCount = wordsCount ** passphraseLength;
const powerOf2 = Math.floor(Math.log2(combinationsCount));
console.info(`Combinations: ${combinationsCount} or 2^${powerOf2}`);
//→ Combinations: 2.2107391972073336e+23 or 2^77
Learn more: EFF Dice-Generated Passphrases
By the way, many cryptocurrency wallets including Bitcoin use equivalent strategy for backup keys. The standard is called BIP39 and uses 2048 english words for passphrase generation.
World Password Day
Taking into account that in average user has around 100 passwords for different websites and apps, updating all of them can become a real pain. Some say it's a good practice to update all your passwords every several months or once per quoter. Others suggest updating even more often.
It's all up to you when to update your entire wallet or credentials for particular service, but there's one rule of thumb that everyone should follow: World Password Day.
Introduced by Intel6, it has place yearly on the first Thursday of May. And although it's not an official and widely accepted date, we use it as a reminder of the important role that passwords play in our digital lives.
So don't hesitate, save the date to your calendar and update all of your passwords at least once per year. I follow this way, though I update many of my credentials more frequently.
Useful links
Footnotes
-
https://dropbox.tech/security/zxcvbn-realistic-password-strength-estimation ↩
-
https://github.com/danielmiessler/SecLists/blob/master/Passwords/Common-Credentials/top-20-common-SSH-passwords.txt ↩
-
https://www.eff.org/deeplinks/2016/07/new-wordlists-random-passphrases ↩
-
https://community.intel.com/t5/Blogs/Thought-Leadership/Big-Ideas/Celebrating-the-8th-Annual-World-Password-Day/post/1335057 ↩